Access Control
Manage user roles, server access, and fine-grained element permissions.
Edison Watch provides a flexible access control system to manage what users and roles can do with AI tools.
Core Concepts
Access control is built on three pillars:
- Roles: Collections of users assigned a specific label (e.g., "Developer", "Support").
- Server Enablement: Controls which MCP servers are available to specific users or roles.
- Element Enablement and Permissions: Fine-grained control over specific tools, resources, or prompts.
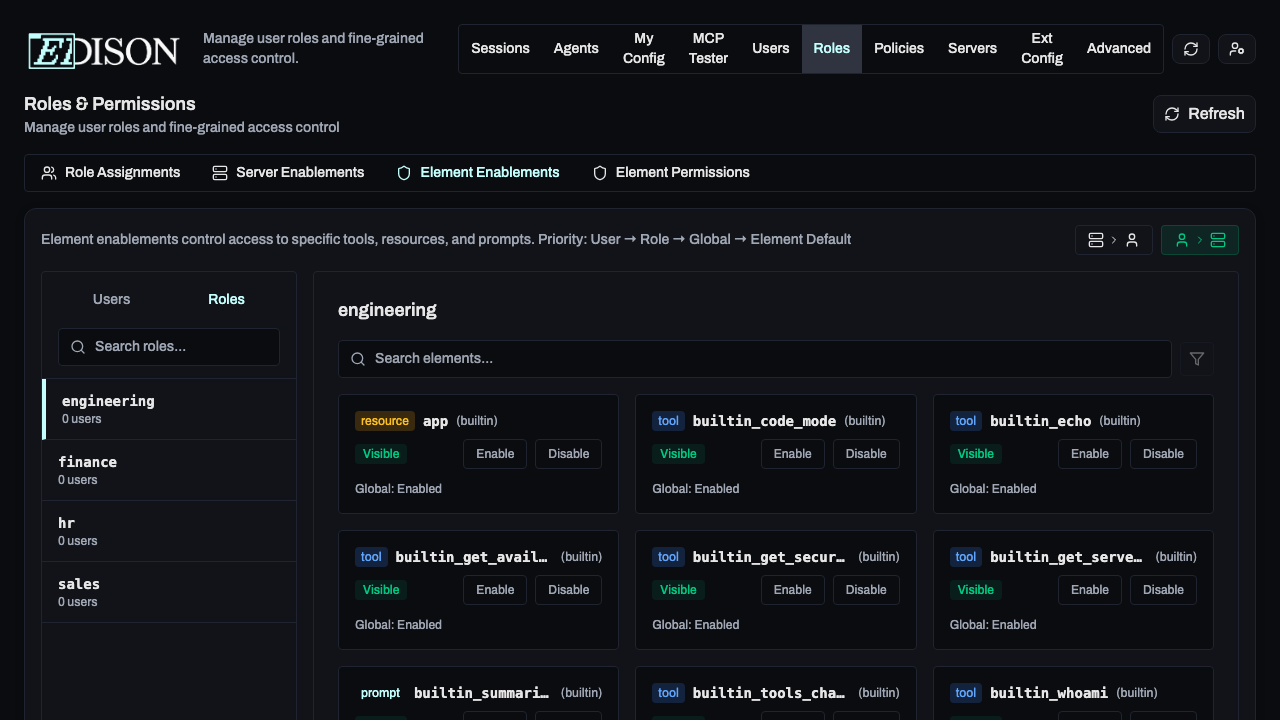
Managing Roles
Go to Roles in the navigation bar to manage role assignments.
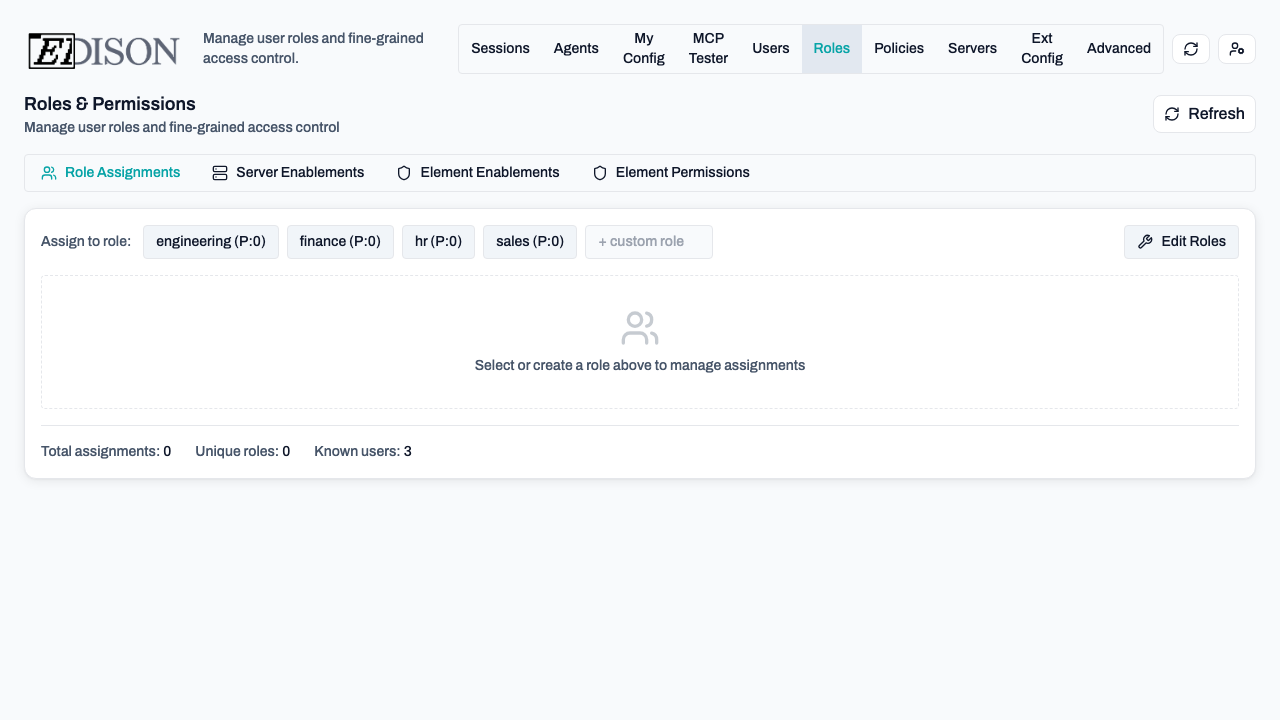
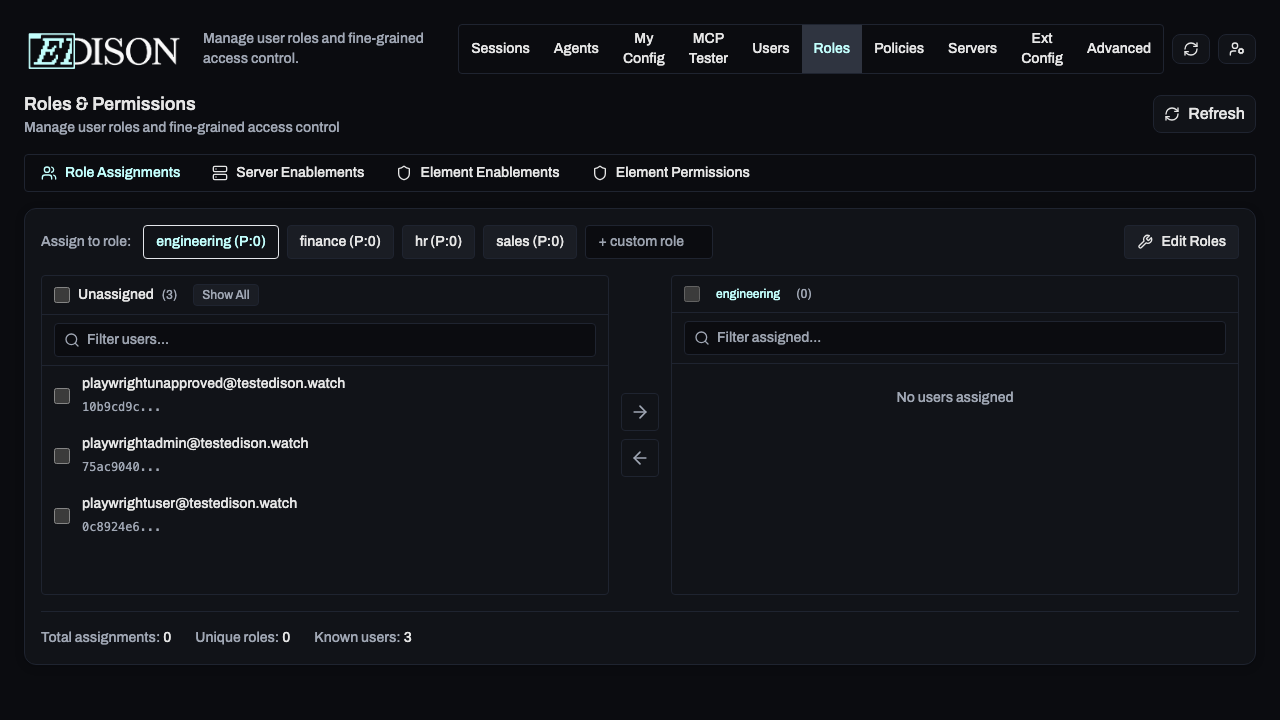
Assigning Users to Roles
Use the Role Transfer List to assign users:
- Select a role from the list or create a custom one.
- The Unassigned column shows users not in this role.
- Select users and click the Right Arrow to assign them.
- To remove, select users in the Assigned column and click the Left Arrow.
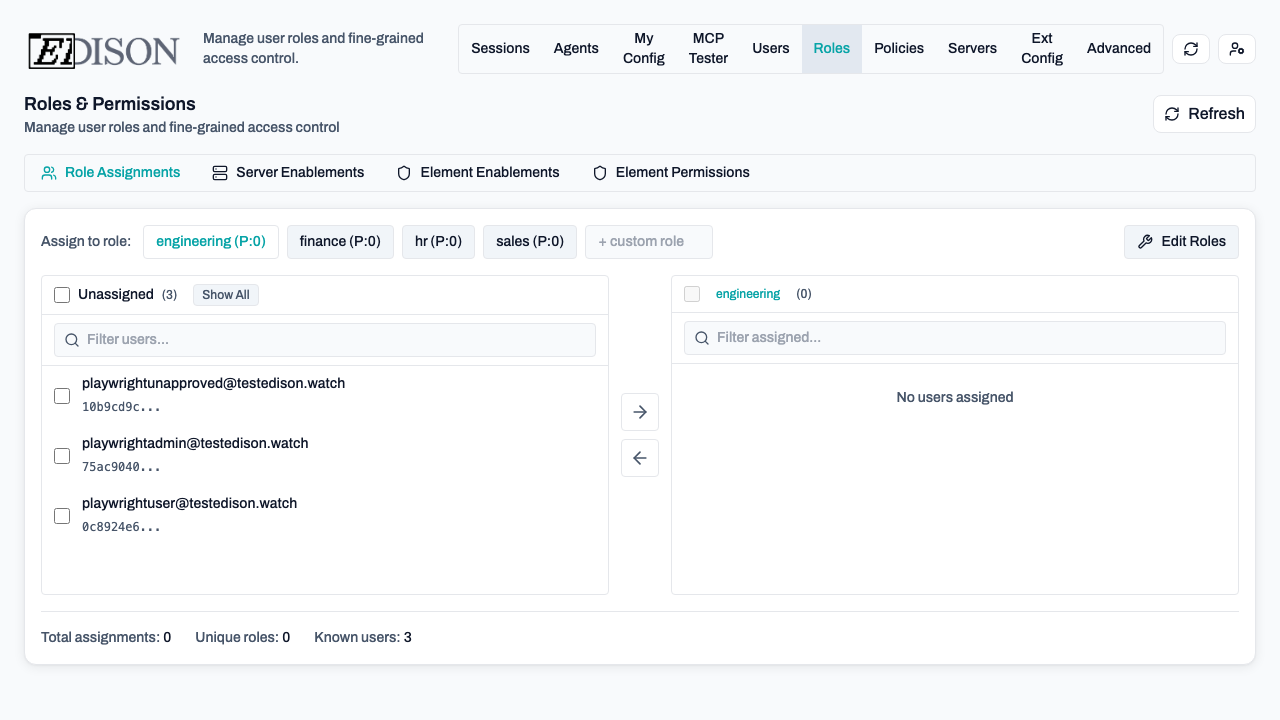
Users can belong to multiple roles. Permissions are additive.
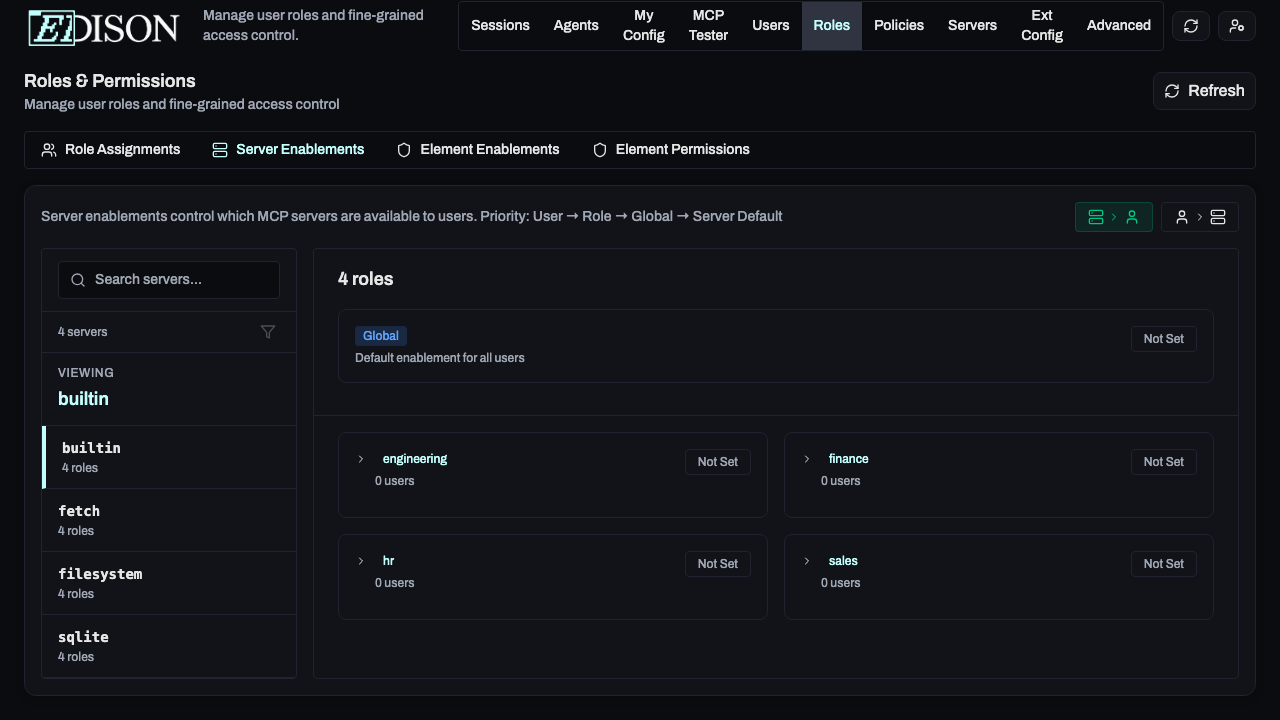
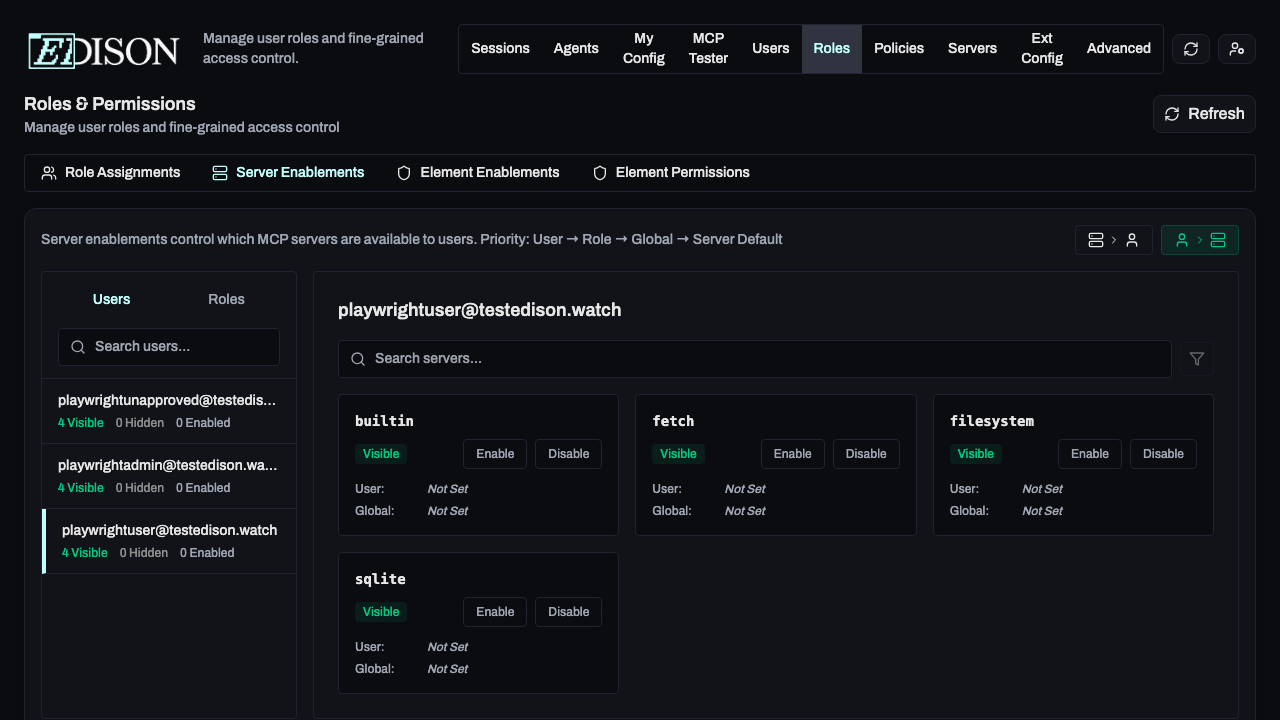
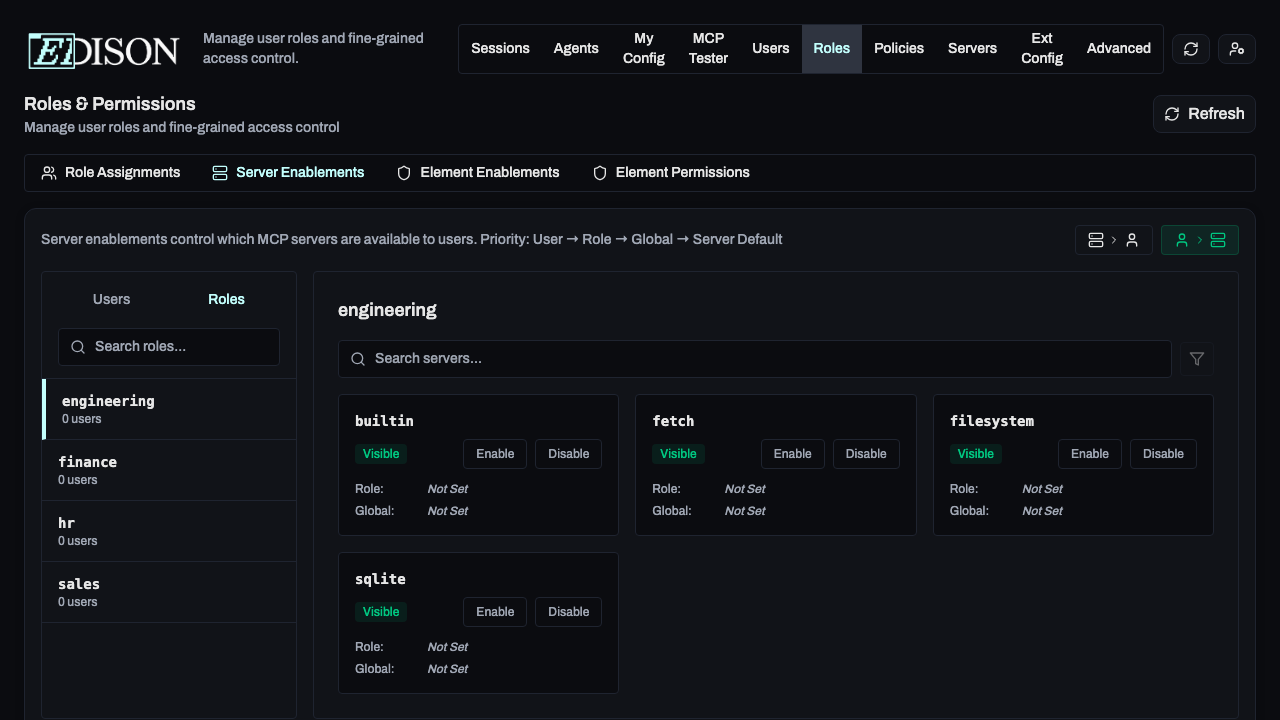
Server Enablements
Control server access at the organization, role, or user level.
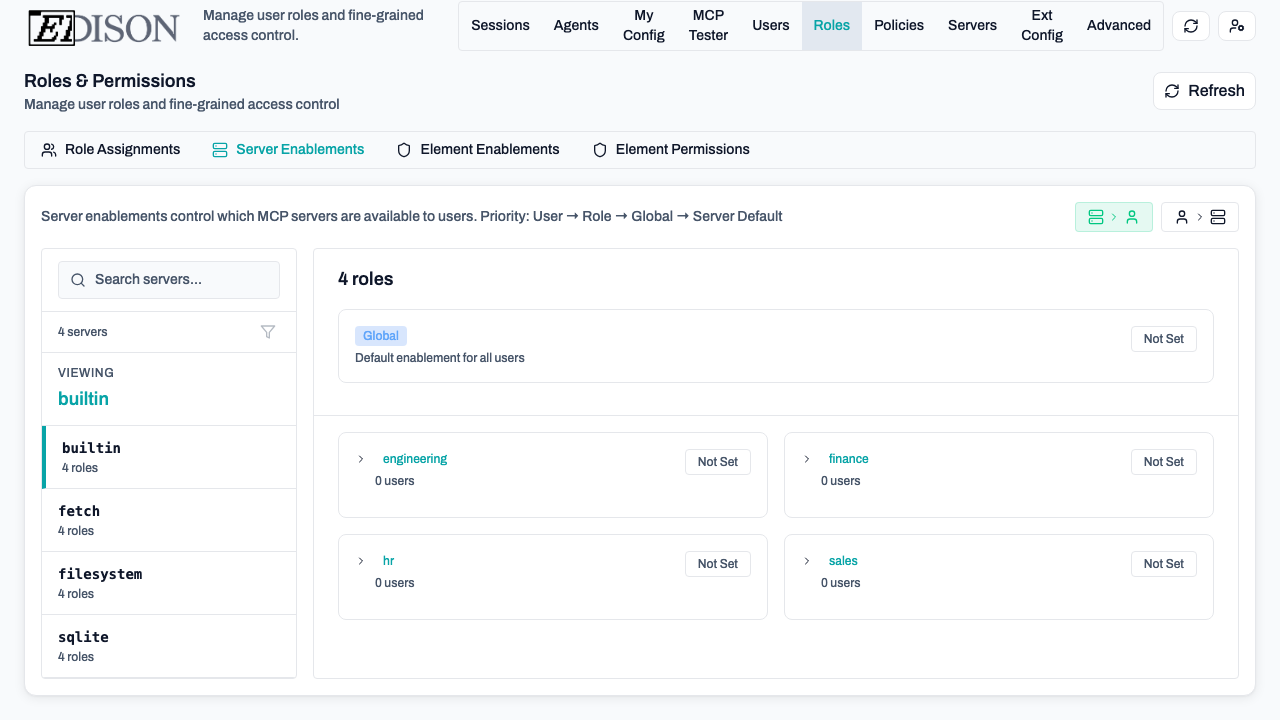
Organization Level
In the Servers page, enabling/disabling a server sets the global default. When a server is disabled globally, then by default it will not be visible or accessible to any users or roles. This can be overridden at the role or user level (more on that below).
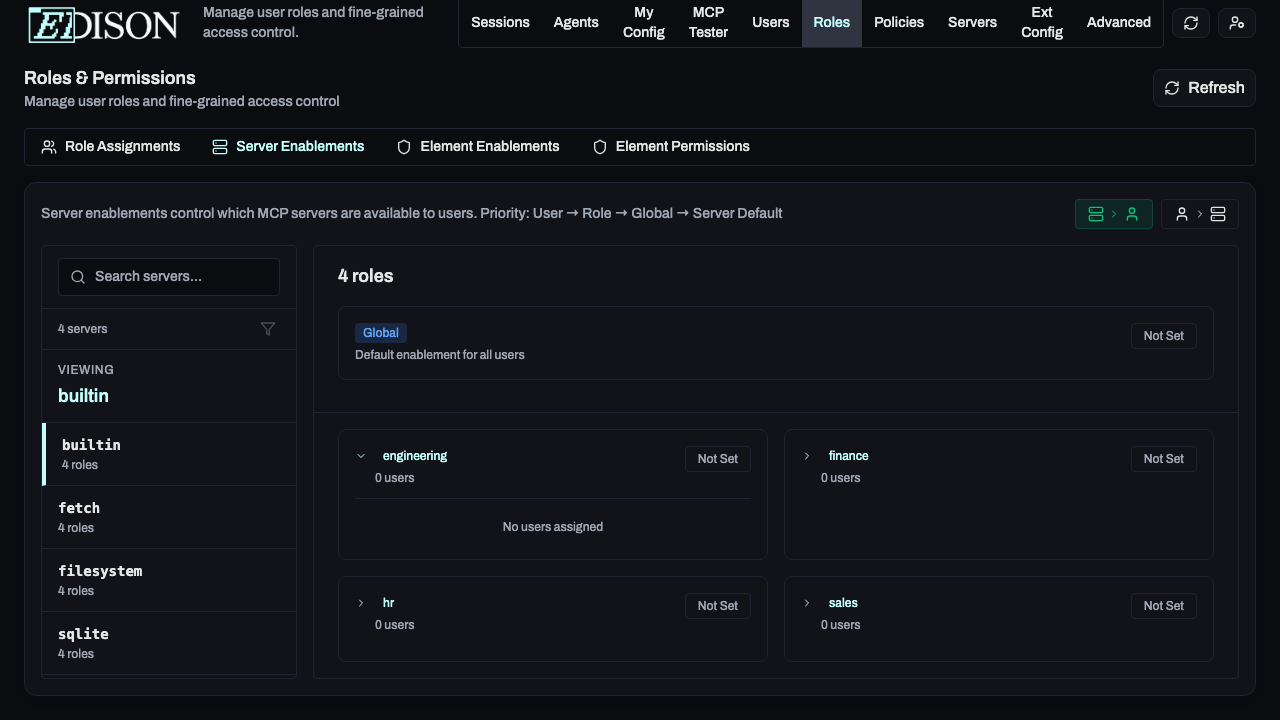
Fine-Grained Server Access
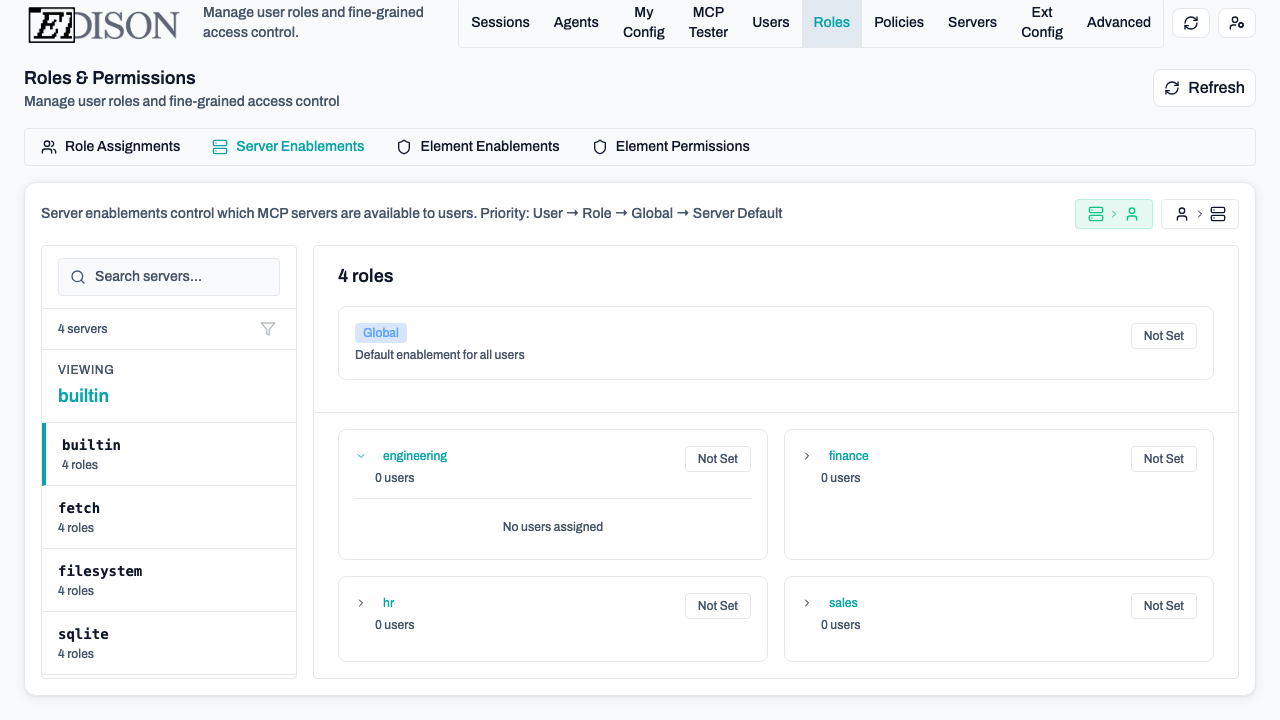
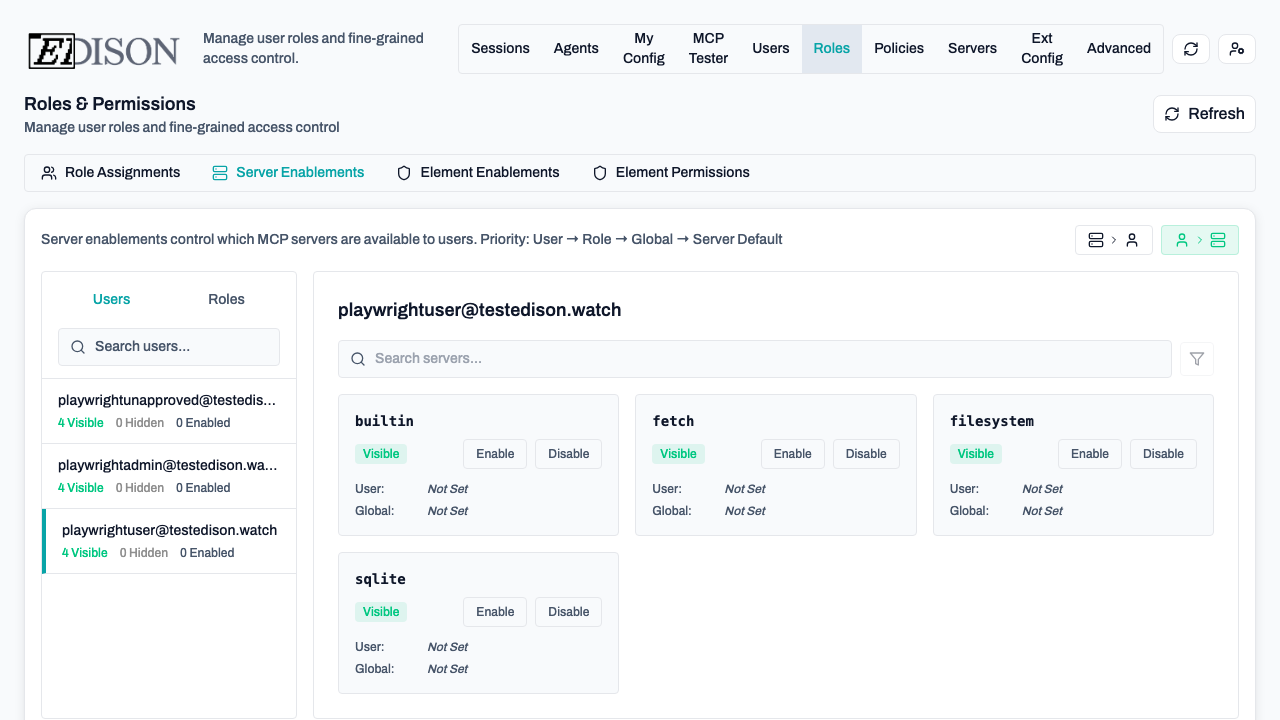
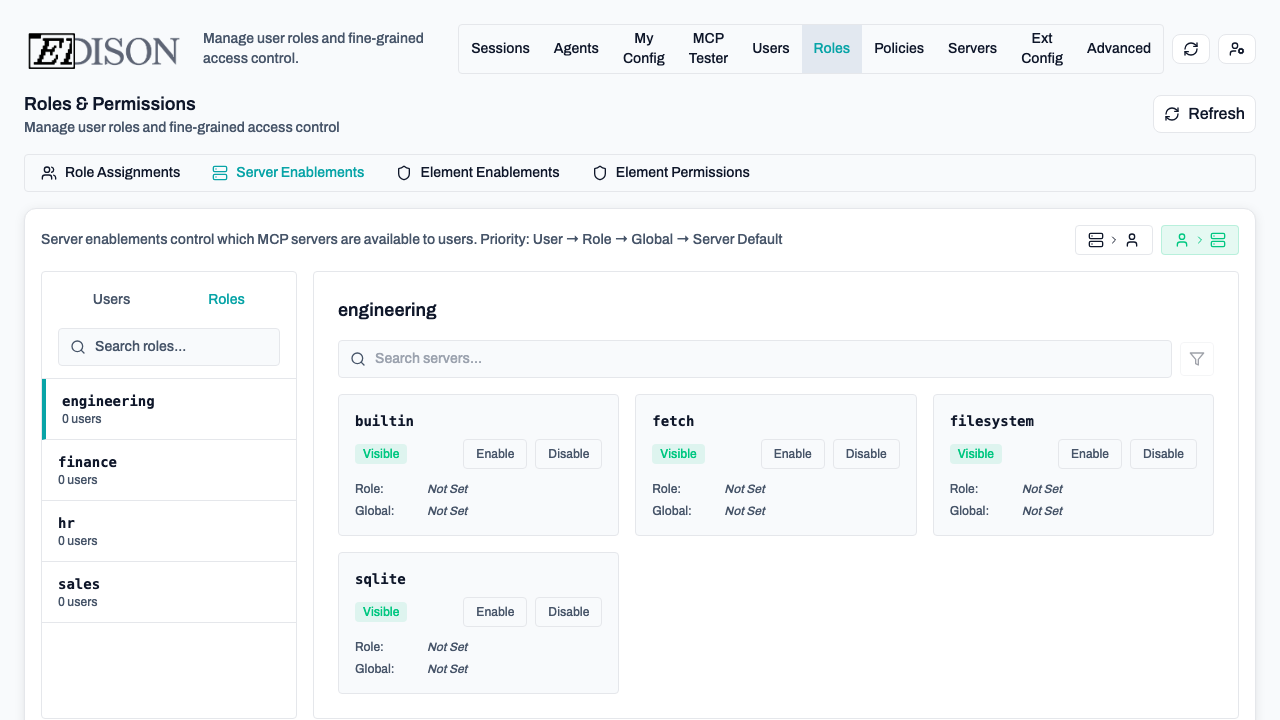
In the Roles → Server Enablements tab, you can override defaults:
- Server-to-User View: Select a server to see and change which users/roles have it enabled.
- User-to-Server View: Select a user/role to see and change which servers are enabled for them.
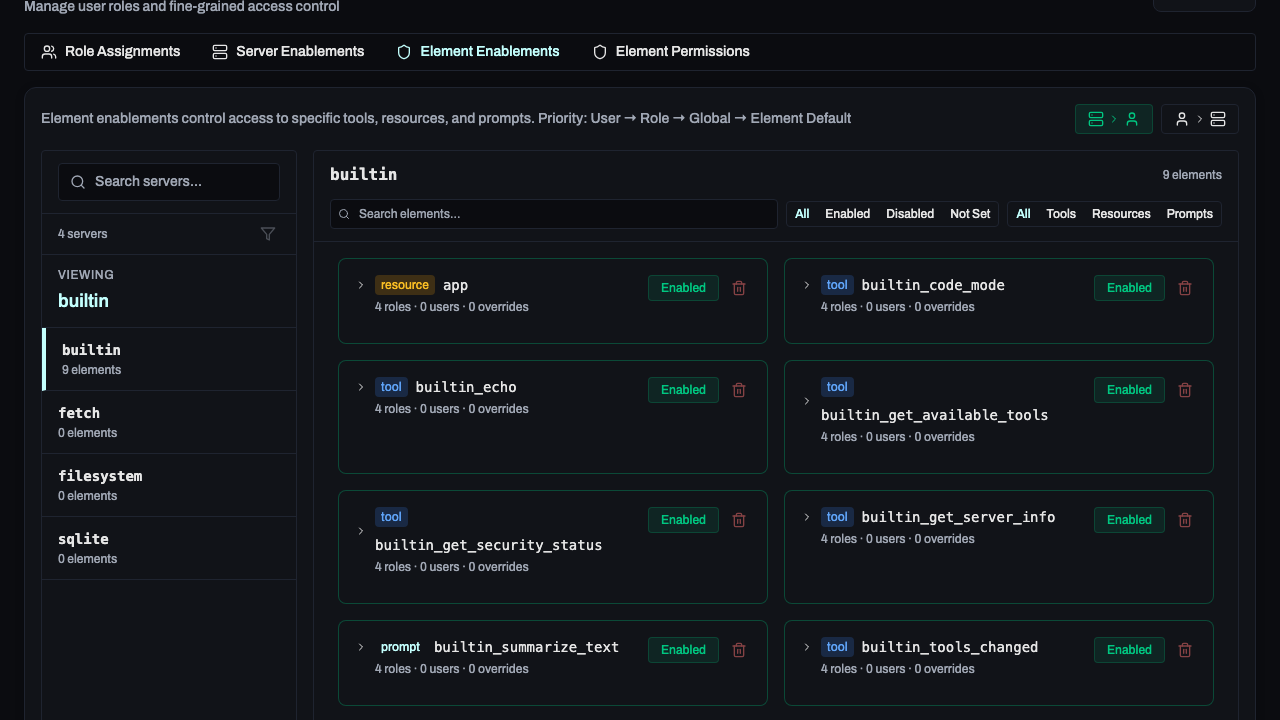
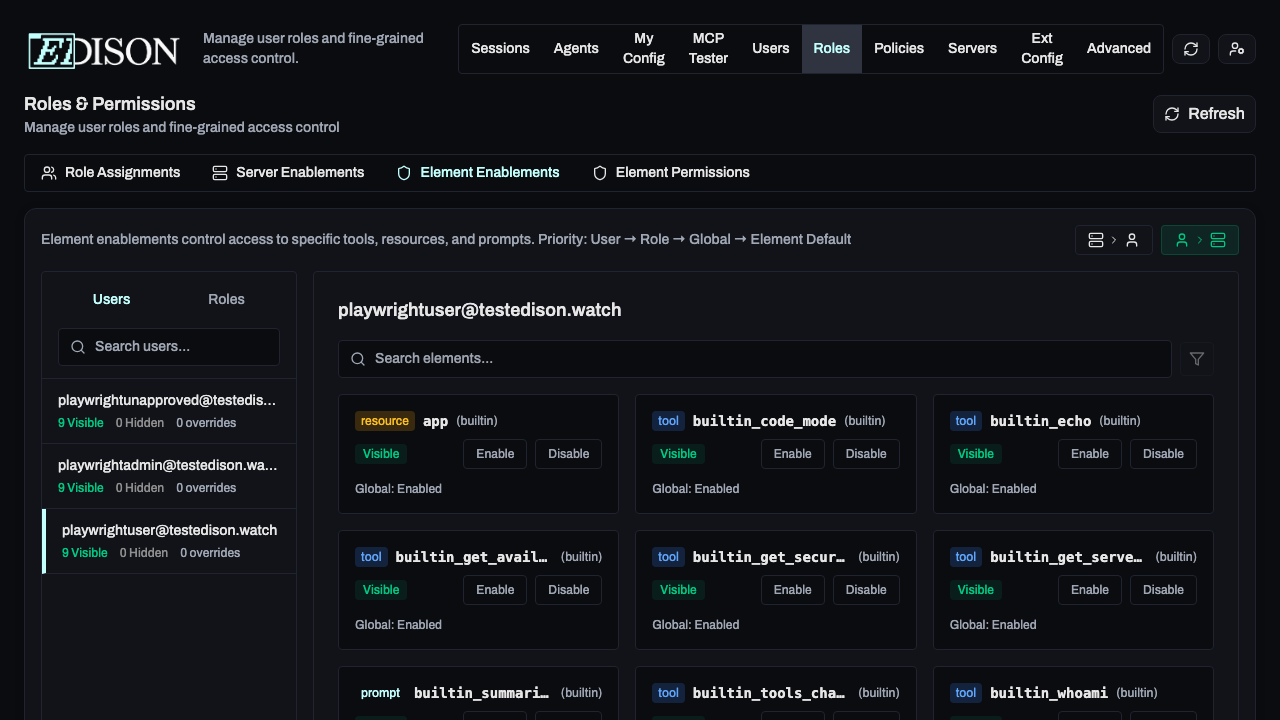
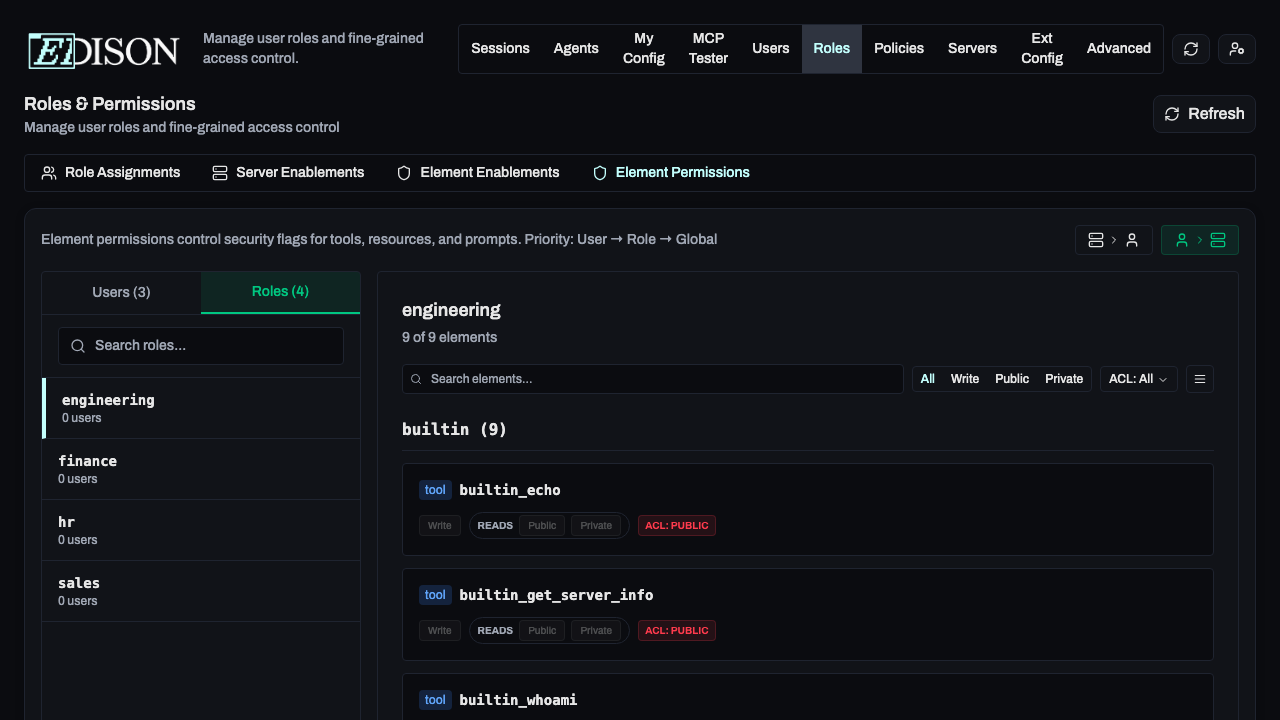
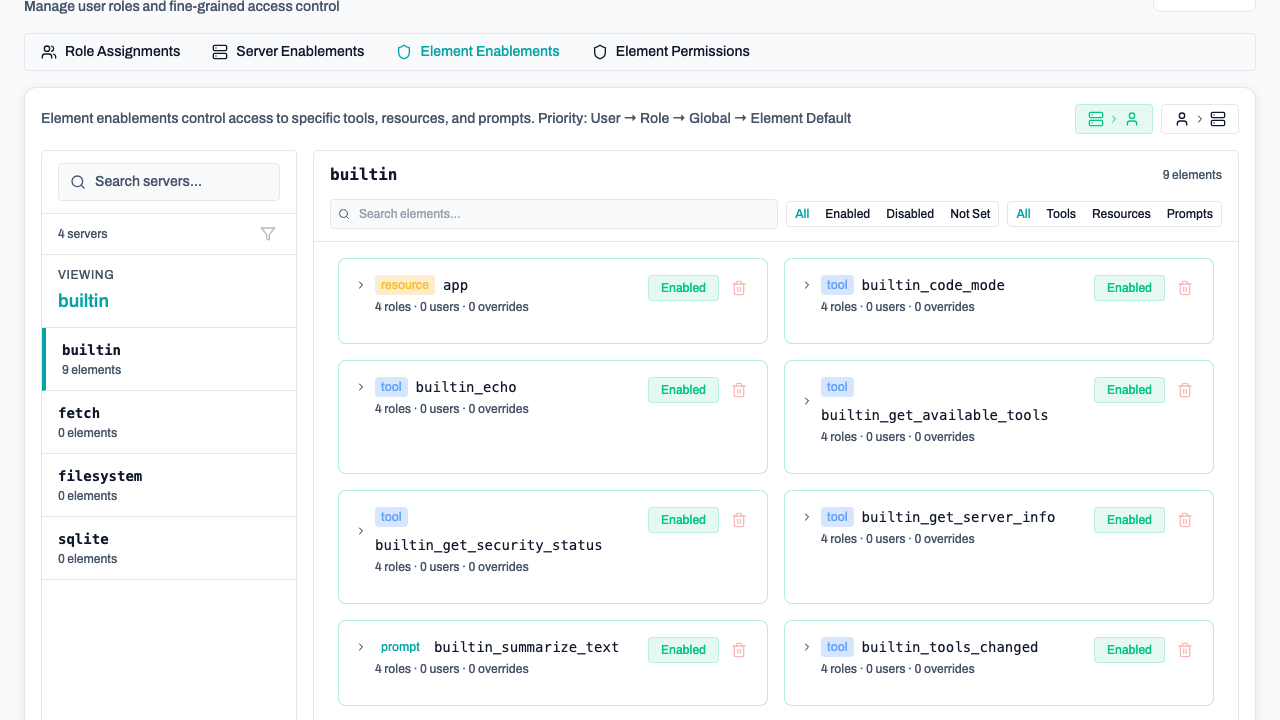
Element Enablements
For maximum security, you can control access to specific tools (e.g., only allowing certain roles to use delete_file).
Go to Roles → Element Enablements:
- Select a server from the sidebar.
- Locate the specific tool, resource, or prompt.
- Toggle access for specific users or roles.
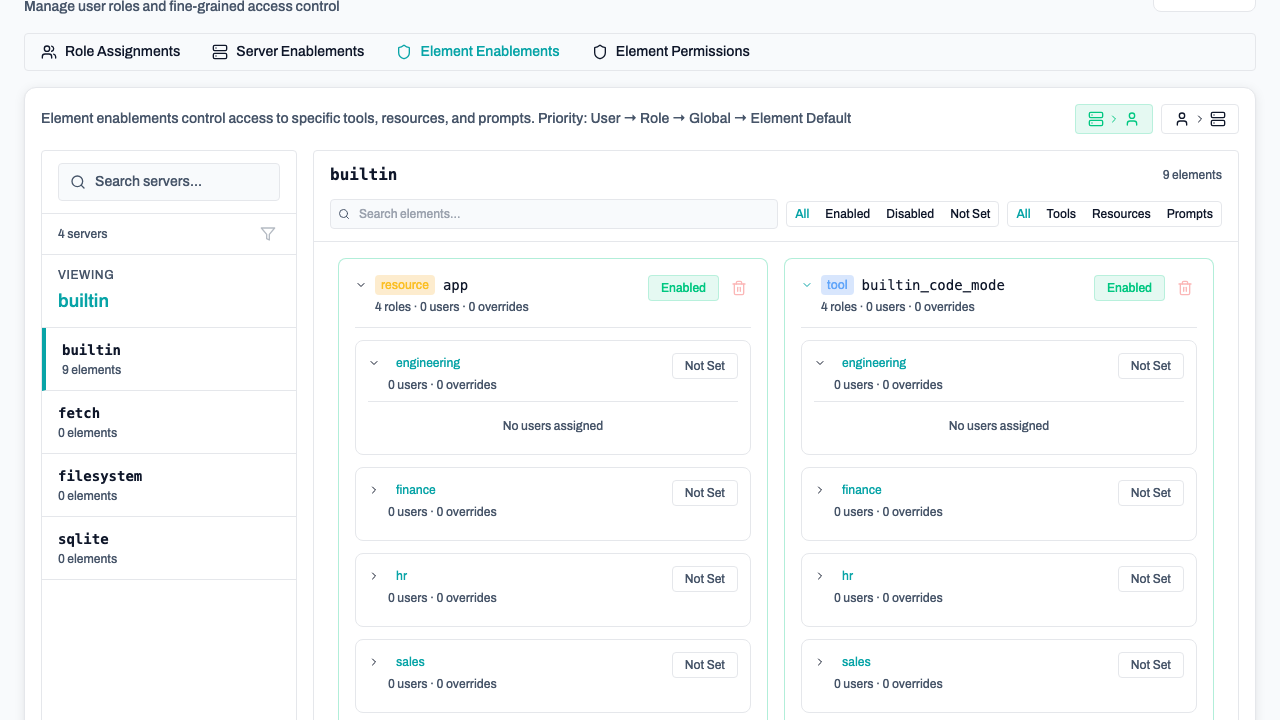
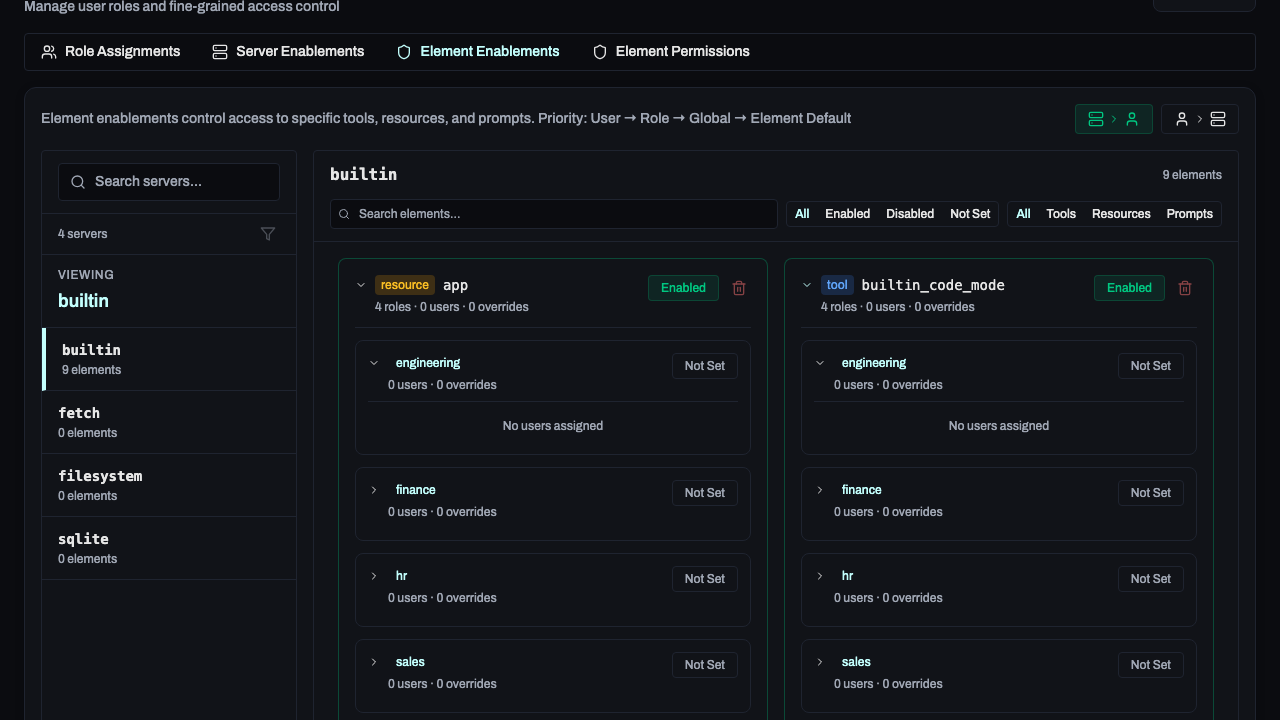
Fine-Grained Element Access
In the Roles → Element Enablements tab, you can override defaults:
- Server-to-User View: Select a server to see and change which users/roles have it enabled.
- User-to-Server View: Select a user/role to see and change which servers are enabled for them.
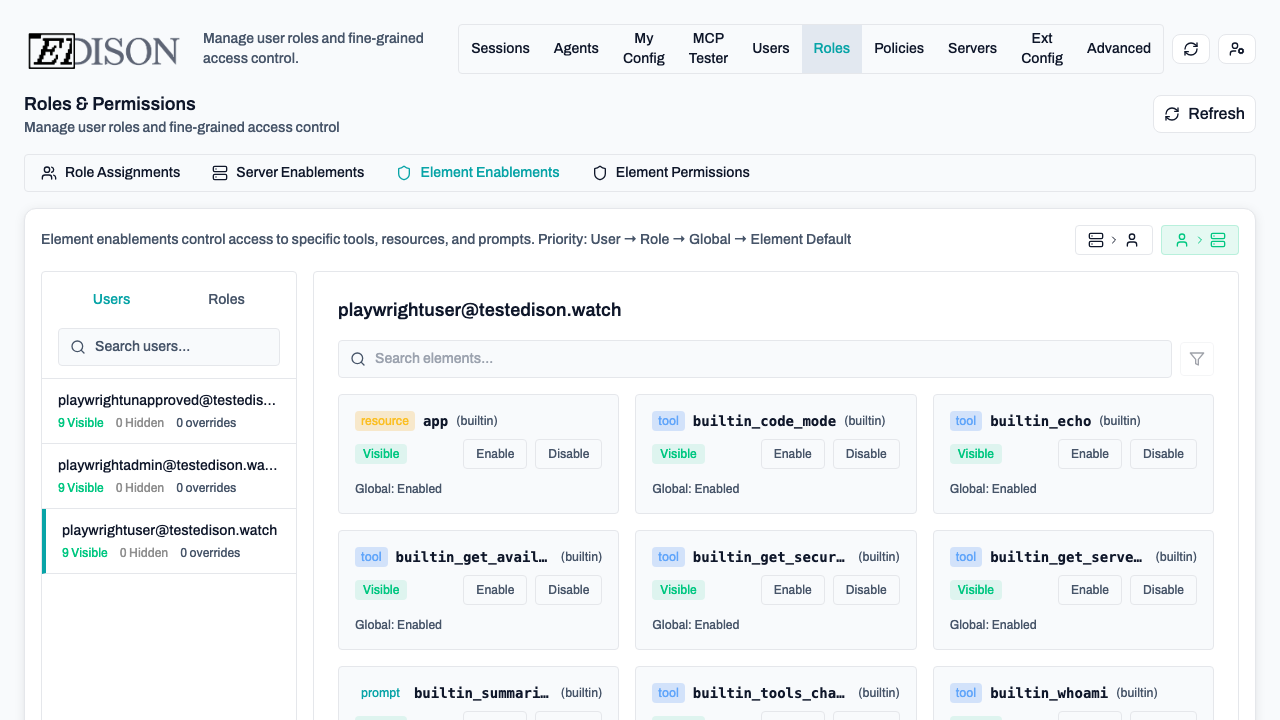
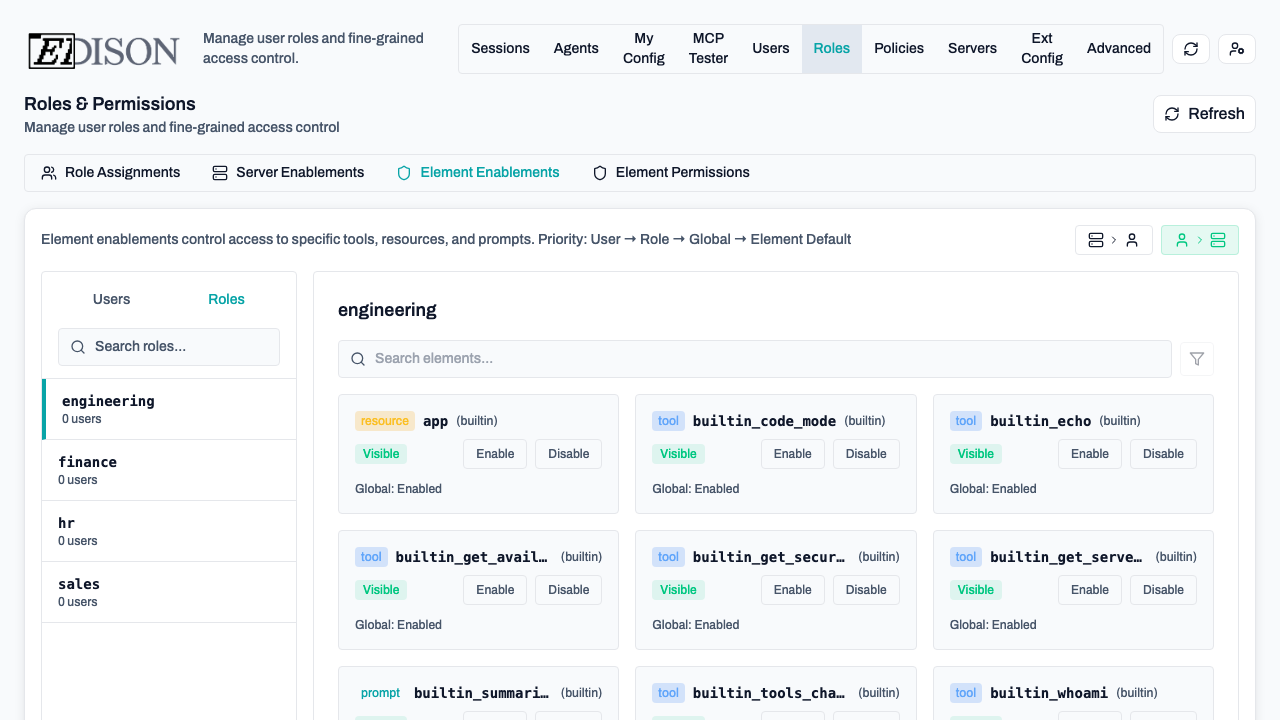
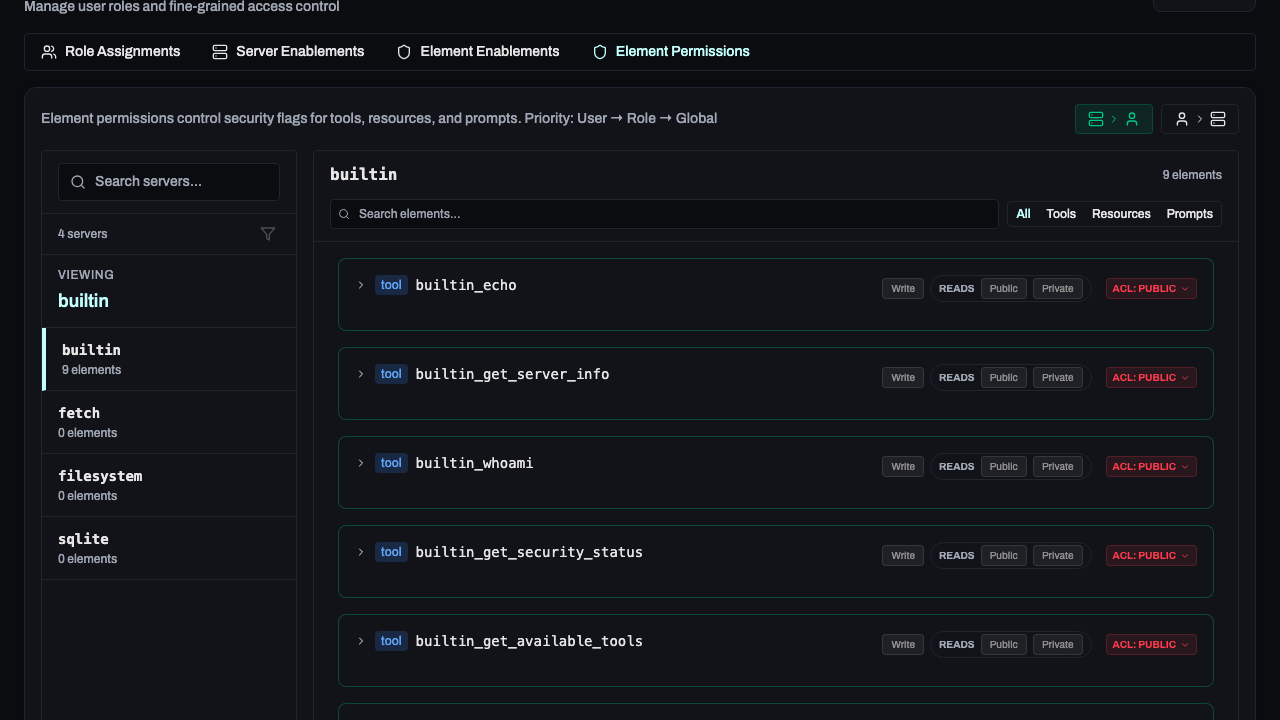
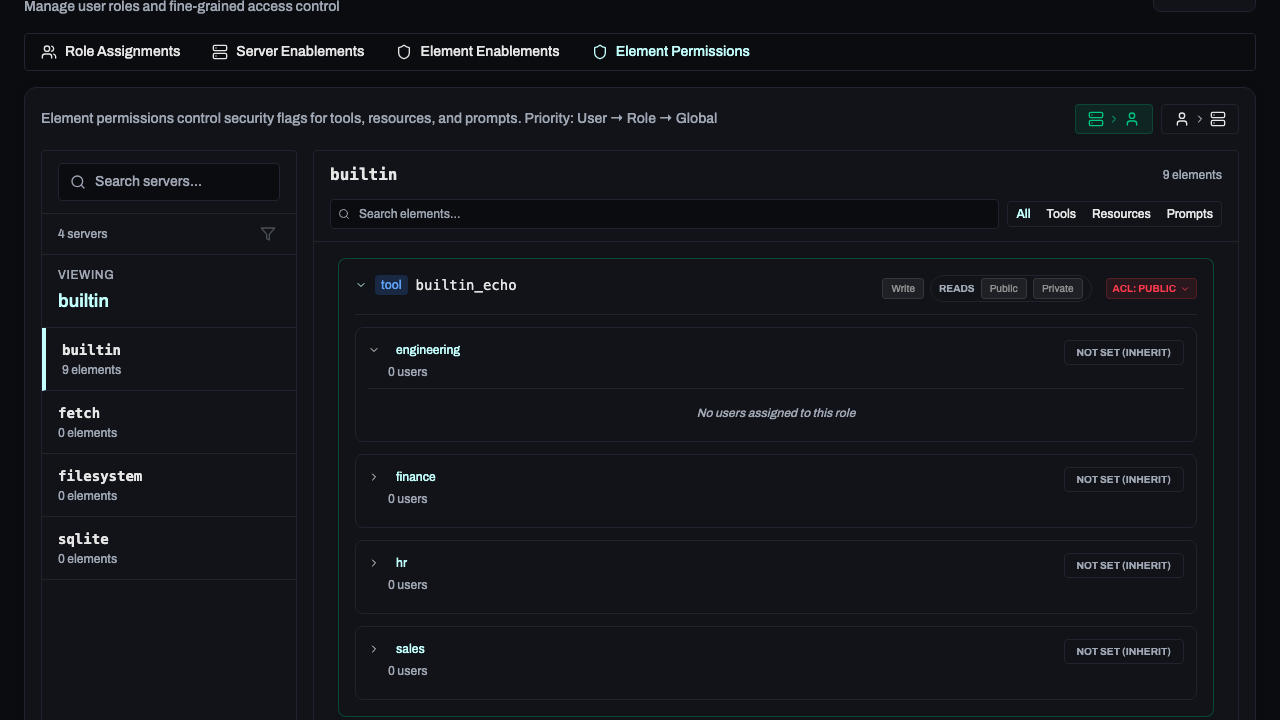
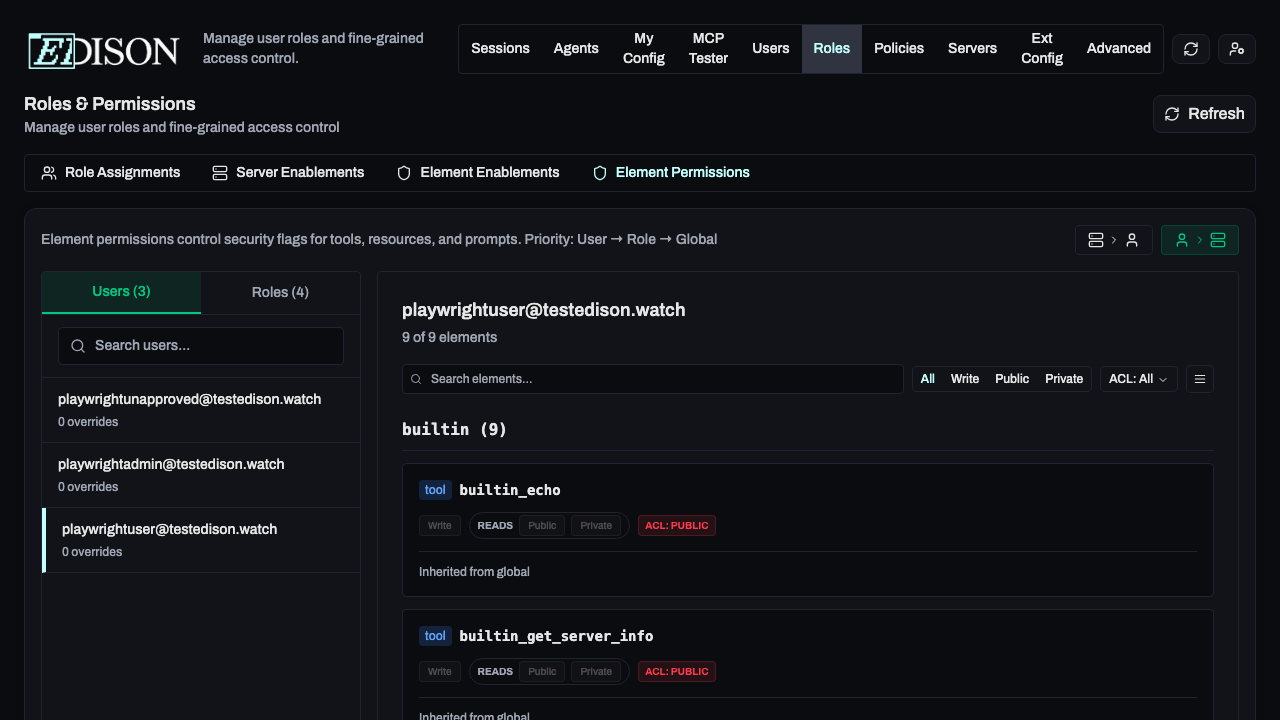
Element Permissions
Fine-grained permissions allow you to control the specific actions that users or roles can perform on specific tools, resources, or prompts.
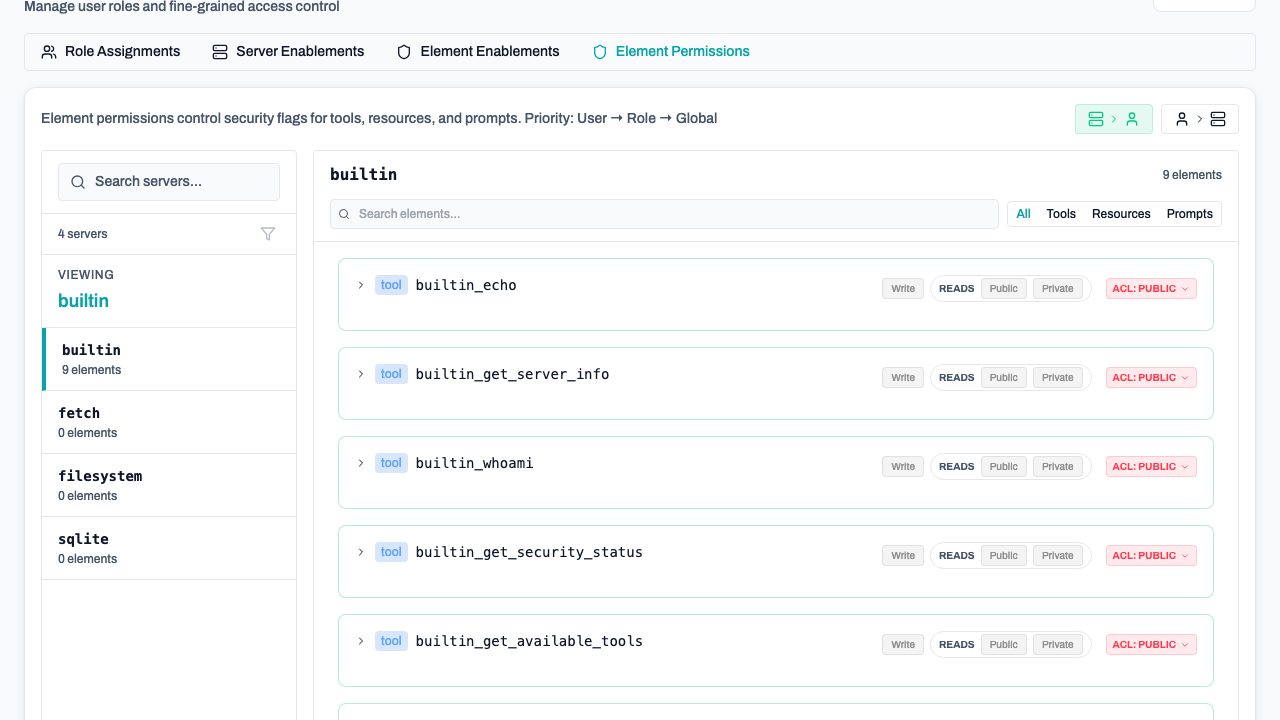
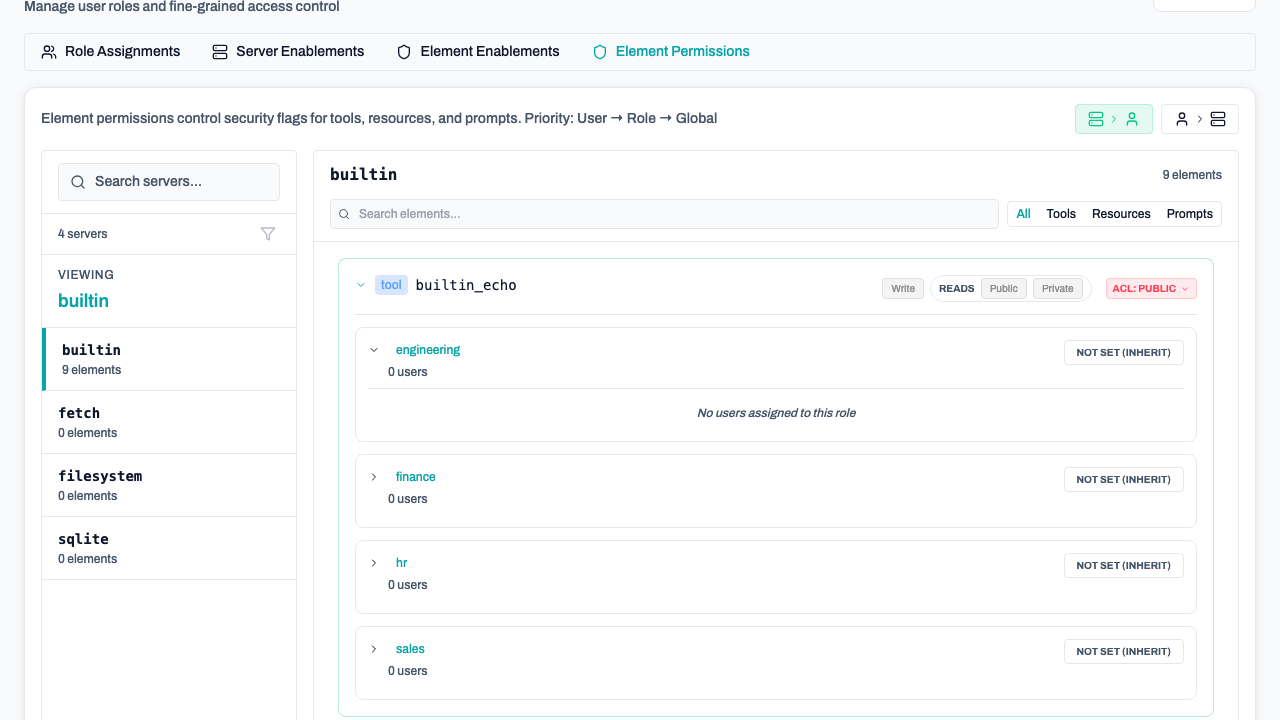
Element permissions are evaluated in the following order:
- User-specific permissions
- Role-specific permissions
- Global permissions
Role-specific permissions are evaluate based on the roles' priority. The highest priority role's permissions will be used.
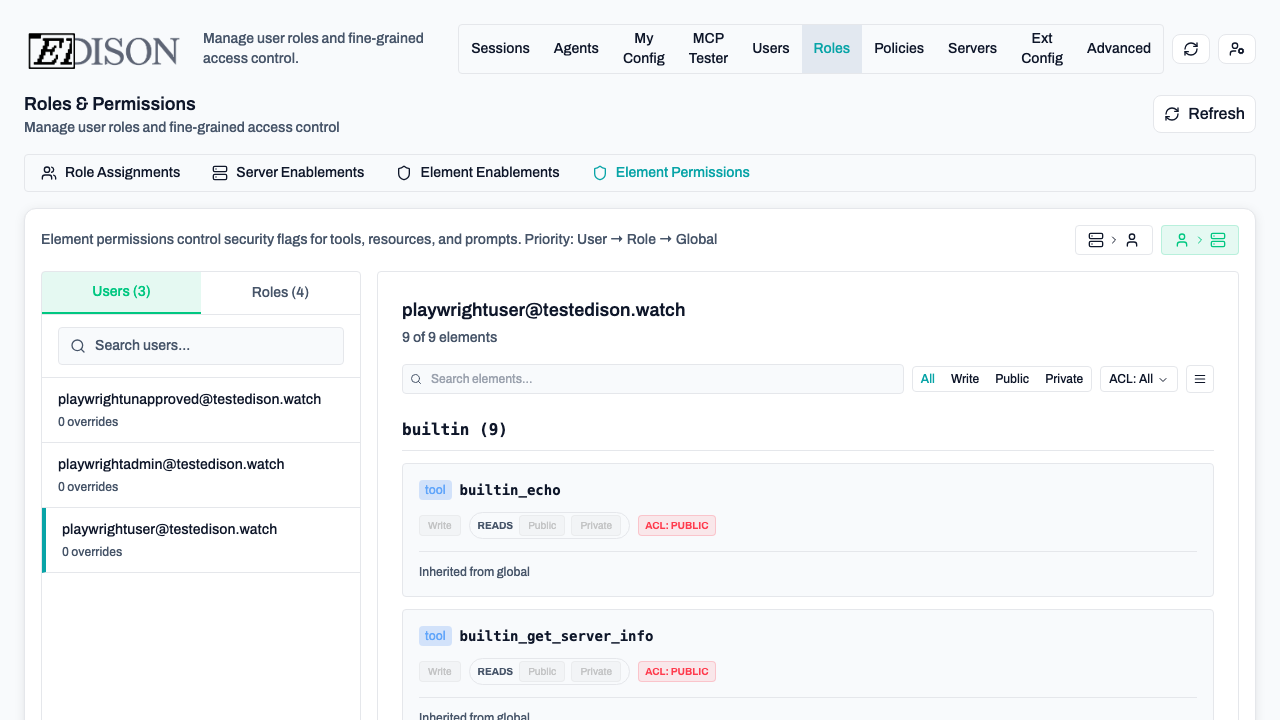
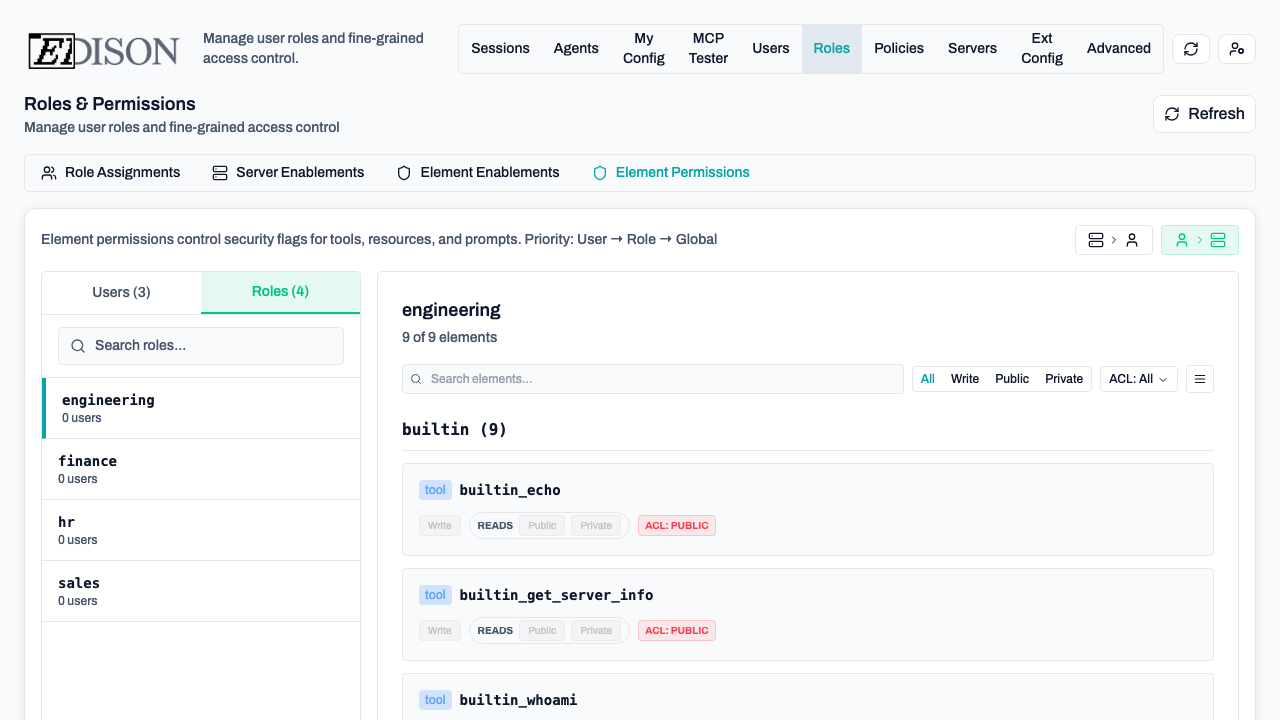
In the Roles → Element Permissions tab, you can override defaults:
- Server-to-User View: Select a server to see and change which users/roles have it enabled.
- User-to-Server View: Select a user/role to see and change which servers are enabled for them.
Need more advanced control? See Policy Rules (CEL) for building complex logic based on tool arguments and user identity.